SSH provides remote access to the command line interface of your server. Via this interface you have full control over your server the services and sites hosted on it. If a hacker gets access to your server via ssh then they have full control – it needs to be secured.
There are several ways that ssh access can be secured. This blog post is based on how we secure our servers which are based on Ubuntu and Plesk Oynx.
You will need to be able to ssh to your server, Mac users can use the ssh command, PC users will need to download an ssh client such as Putty.
Create a root user
You still need remote access via ssh to your server so we need to create an account.
- Log onto your server via ssh: ssh root@hostname or IP
- Enter the command adduser newusername
- Enter a secure password and confirm
- You will then prompted to enter some additional details, this is optional
- Now we need to add the user to the sudo users group, this the group that allows root access, enter the command usermod -aG sudo newusername
- Test the user, enter the command su – newusername
- Enter the command sudo ls -la /root (this is only accessible to a root user)
- Enter the password for newusername
- If you have created the new user correctly this command will execute correctly.
Disable remote root login
The next step will prevent root from being able to login remotely via ssh. You will still be able to use root from a console session or the physical server screen:
- ssh to the server using the new user name
- Open the ssh configuration file with your preferred file editor: nano /etc/ssh/sshd_config
- Find the line #PermitRootLogin No and change to PermitRootLogin No
- Save the file
- Restart the ssh service with the command sudo service ssh restart
Change the SSH port
Note: you must remember if you have a firewall setup you need to update this allow access, check with your provider that you can change the default port. Also remember that if you have multiple servers talking to each other via port 22 you will need to update these. If you are not comfortable or confident that this change will not affect your access or infrastructure then skip this step and implement the additional security steps below.
The default port for SSH is 22, to improve security you could change this to something different:
- Decide on the new port number for ssh
- Configure any firewall that you have setup to allow this port through
- Open the ssh configuration file with your preferred file editor: nano /etc/ssh/sshd_config
- Find the line #22
- Remove the # and change the port to the port number you have choosen
- Save the file and restart the ssh service with the command service ssh restart
Additional Security
Static IP Address – Limit access to ssh via Plesk Firewall
If you have a static IP then you can limit ssh to the IP of your internet connection via the Plesk Firewall Extension, this blog assumes you have already followed the 4 Steps to secure your Plesk Sever
- Login to your Plesk Control Panel
- Click on Tools & Settings
- Click Firewall
- Click Modify Plesk Firewall Rules
- Click SSH (Secure Shell) Server
- Select Allow from selected sources, deny from others
- Enter your IP address
- Click Add
- Repeat for all the IP addresses you want to allow access from
- Once you have added all the IP addresses click OK.
- Click Apply Changes
- Click Activate
You will now only be able to access your server by SSH from the IP addresses you entered.

Secure Access via Duo
If you do not have a static IP you can add an additional layer of security to ssh using Duo. Duo is a 2 Factor Authentication Service that provides 2FA to a range of applications and services. Even if you have a static IP we recommend you add this additional layer of security. First you will need to head over to https://duo.com and create a free account and carry out the steps below.
- Create a user with the same name as the user you have setup for ssh access and follow the instructions to setup notifications.
- Modify the global settings so that for New Users to Deny access to unenrolled users.
- Click Protect an Application and select Unix, leave this screen open and carry out the steps below on your server.
- ssh to your server
- Enter the following command: nano /etc/apt/sources.list.d/duosecurity.list
- Enter the text deb http://pkg.duosecurity.com/Ubuntu trusty main
- Save and close the file
- Enter the following command: curl -s https://duo.com/APT-GPG-KEY-DUO | sudo apt-key add –
- Install the Duo software with the command: sudo apt-get update && sudo apt-get install duo-unix
Once the application is installed we need to configure it with the information from Duo:
- Edit the configuration file: sudo nano /etc/duo/login_duo.conf
- Enter the Integration Key, Secret Key and API hostname as required
- Save the file and exit
- Edit the ssh configuration file: sudo nano /etc/ssh/sshd_config
- Add the following line to the end of the file: ForceCommand /usr/sbin/login_duo
- Save the file and exit
- Set the permissions on the login_duo.conf file: sudo chmod 600 /etc/duo/login_duo.conf && sudo chown sshd /etc/duo/login_duo.conf
- Test by typing: login_duo if all is working you will see something similar to the screen shown below:
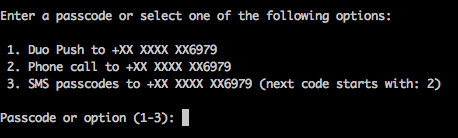
- Enter 1 you should receive a push notification to your phone, approve the login
- If all works ok, restart the ssh service: sudo service ssh restart
- Logout and now every time you login you will be prompted via your 2FA.
SSH access to your server is now secured. You have disabled remote access by the root access and either implemented restricted access based on IP and or 2 factor authentication. Securing your server is only one of the ways that you should secure your server, remember to keep your server up to date and backed up.
All the servers we setup and manage have 2FA implemented on ssh and are kept up to date and backed up – if you need any help or advise on securing your Plesk server do not hesitate in contacting us. If your provider is not implementing these services for you, or is not able to provide them for you – then contact us.
Contact Us



